Digital Saints Solutions News & Blog
5. Educate Employees, Friends, Family & Request Professional Assessment
This is the best tip we can give you, because most attacks are on the most vulnerable aspects of our security protocols and no amount of patches, hardening, or software updates will stop us from being the weakest leak.
Humans naturally make mistakes. With data security and overall security in every sense of the word on both a large several and on a personal level, it starts with education, progresses to understanding, and then prevention.
To this day, scam emails and phishing have cost Americans millions each year and many of these scams go unreported and unresolved. It is estimated that 38% of Americans will be scammed in their lifetime and that number is trending upward. On average, each scam earns the scammer around $535, but 27% of this statistic report losses of $1000 or more.
In 2024, consumers reported $12 billion in fraud in the USA, a 25% increase from the previous year, according the FTC.
These breaches are the result of social engineering and phishing - and these things aren't covered by anti malware or antivirus software. It often starts with some kind of incentive or a threat. The scammer will often use legitimate credentials and some information they may have gleaned to make themselves seem like a valid agent or associate of a business.
Even worse, scammers pose as friends or love interest, scouting dating sites and social media for victims they exploit through manipulation and blackmail to pay them 'or else', with some cases recently involving kidnapping.
- Scammers use fake social media profiles and photos to attract the victim, appearing often as someone they know or have seen on others friends lists. They will target anyone, choosing photos and words carefully to make their persona believable. Often, several scammers will interact with the victim of the course of the relationship under one profile.
- Scammers will use dating sites and classified ads to exploit singles and those seeking any form of a relationship, pretending to have genuine feelings for the victim while grooming them to perform specific actions, such as sending money via Western Union, paying for travel or accomodations and cancelling plans last minute while pocketing the funds given, requesting 'pity payments' for disaster relief, hardships, or personal misfortune that is fraudulent / unfounded.
- Posing as legitimate businesses is also very common, particularly in phishing attempts. Bad actors will falsify login and payment pages, tampering with the url just enough so that it appears real, using email address or identities that, at first glance, appear to be legitimate but can not be verified beyond one on one interactions.
- Blackmail, threats, and coercion are also on the rise. While scammers rarely operate on the same continent as their victims, there have been recent reports of kidnappings and puppeteering of other victims, utilizing them as couriers and proxies for their activities, allowing them to operate incognito and the victim taking all the risk of the transaction if caught.
While you cannot 100 percent guarantee mitigation of these very human threats, through education and regular communication, companies and businesses can build a stronger human Frontline against those using these tactics.
At home, those born prior to the 1970s are more at risk simply due to lack of exposure and a general lack of education in current risks with technology. Children are also very vulnerable and internet usage / social media should be restricted and monitored based on what is appropriate for you and your child, their maturity level, and overall understanding of potential risks that can affect them just as much as anyone else..
Here are our tips to help fill the gap in security that hardening and software can't ever fully cover.
- Talk about potential risks, current known exploits or security flaws, and approve communications based on security clearance or with access control in the workplace. Whether you hold regular training seminars or prefer an email newsletter, set up communications that keep your employees in the know as to what risks are out there. Make them aware of any security exploits you may be aware of on a need to know basis, and restrict sensitive information for those with higher security clearance.
- Open up lines of communication in the event a breach is detected or someone expects fraud, phishing, etc. in the event that data is compromised, always move to stop the bleeding first. Remove access or connectivity from your databases to restrict access to them until the exploit is fixed or the breach has been resolved. •Encourage employees to report anything they suspect may have put them at risk or that they noticed during regular operations that did not seem regular. Use instances of breaches as a learning tool for the rest of the workforce as these things are wholly unavoidable and it is more productive to deal with them quickly and without hesitation to mitigate any and all damage in progress or that has been done.
- Encryption and using secure terminals or tokens can be a viable solution for e-commerce platforms, online businesses, and other companies or small businesses that process payments and handle sensitive consumer data transfers regularly. See the bottom of this article for our recommendations and links to relevant solutions.
- At home, discuss current and past instances of scams with family and friends. Do not hesitate to share your own story so that your experience can be learned from. Make note of common circulating phishing scams and known data breaches so you can anticipate what to do next. If your data has been leaked, you may experience suspicious activities on your accounts. Make sure you change passwords regularly and log off accounts in order to kick any bad actors off your account as well.
- Install multi factor authentication or 2FA. Use Passkeys as mentioned before. It is much harder to give away something you can't physically give.
Is Your Data Safe? 5 Ways To Protect Your Personal & Sensitive Data
It's no secret, data breaches happen all the time. In 2024, there were 3158 reported data breaches in the USA, affecting over 1.35 BILLION individuals. The odds are against us when it comes to data security.
- 2024: 3,158 data compromises reported, affecting over 1.35 billion individuals
- 2023: 3,122 data breaches reported, affecting a total of 349, 221,481 victims.
- 2022: 1,802 data breaches reported as exposed records in databases totaling 422.14 million records
The more advanced technology gets, the more advanced bad actors are to get around security protocols and exploit weak points in information system security as well as employee understanding of who may be cleared to access such sensitive data.
This data is trending upward, but it's no surprise that there is a vast difference between the breaches reported and those records exposed or individuals affected.
As we continue to advance into the modern era with AI data collection, virtual trade, e-commerce, and instant, seamless, payments at the touch of a button, it is important that we acknowledge the facts of this reality while also doing our best to protect our own personal data as well as that of our friends, colleagues, and clients.
1. Avoid Using Your Primary Email Address To Sign Up For Anything
We understand that this is a long overdue concept and email forwarding or the use of proxy email is definitely something many of us have done since the beginning of the Internet without understanding the full benefit of doing so.
Nowadays, your email account, much like your social media, can almost literally act as a supplemental social security number or identification. These intangible identification logs are requested often, and now, with social login options allowing you to login through Gmail or Google, your Apple ID, or your Facebook account, you have more than one option aside from entering your email address and password.
The main issue with email based account registration is this allows bad actors one key sense of acquiring a lot of potentially sensitive data if they are able to get into your email account, which is usually not too hard to do
The only way to mitigate this is to create complex, inhuman, and ridiculous passwords that you change often enough to bump potential hackers off your account when you make the switch.
OR
Ask your service provider, set up an alternative free email account through Gmail or another service, and use only that email for sign ups and online purchases.
This way, your primary email (that which may contain important email with tax information, bank account information, security question answers, birth date, etc) is not so easily acquired.
The proxy email address will be used for forwarding. Just like having your regular mail forwarded, email works the same and a proxy email will work similarly.
The address that everyone sees is your proxy or stand in address that functions and looks legitimate - your agent can create one (or as many as you need!) for you for free if you opt for any of our hosting or web services - is under your domain (myemail@mybusiness.com) BUT any email addresses there will appear in your primary email inbox.
Alternatively, you may set up an entirely separate inbox and delegate a small amount of storage for junk or spam mail. This is also something we are happy to do with any hosting or management plan as free webmail email is included up to 25GB and this storage can be split between several inboxes, upgraded, or allocated to one.
Gmail is our pick for setting up a proxy or forwarding address. You can also read about having email forwarded to your current Gmail account and vice versa here.
You don't have to take our word for it in regards to this growing problem, but we currently have a few measures already in place to help keep our client's data secured, such as:
- Unlimited Forwarding Addresses with Domain purchase and Web Management or Design services, Provided by our partners at Dreamhost.
- Primary @yourdomain.com business or personal webmail (access your email online any time via the Dreamhost login panel) included - 25GB storage, up to 5 free inboxes.
- Google Workspace integration for small businesses for data security and digital asset security
- Security Suite integration for public databases and web databases
- Virtual Private Server and Dedicated Servers run by your trusted agents with security protocols and 24
- hour remote monitoring
- Non US based and US based data centers. Different regions have more robust protocols. We take advantage of this by shifting our data between data centers to prevent remote location by bad actors and brute force attacks.
- Encrypted Payment and sensitive information portals to protect our clients data. We offer several secure and trusted payment portals, working with the best and most reputable payment processing providers on the Internet to date. We recommend the same providers and solutions to our customers.
2. Change Your Password Often and Use Passkeys Wherever Possible
Ask yourself - do I hate having to change my password all the time only to request a new one because I can't keep track of them? Unfortunately, this is the reality for many businesses and even large corporations.
The password requirements often get to points where the necessary combination of letters, numbers, and symbols is impossible to remember, creating a need for constant recovery and backup efforts that can be exploited by social engineering or phishing attempts.
We have a solution for you and all it takes is your smart phone and a pre-set fingerprint or facial recognition setting.
Chances are you use some kind of bio metrics throughout your daily life. Whether you prefer fingerprint unlock or facial recognition, these safety measures can extend beyond just your smart phone or tablet.
Passkeys are viable, phishing resistant security measure that you may have opted into or at least have seen the suggestion to use this type of log in recently.
Passkeys are a form of password-less, often biometric (facial recognition or fingerprint), security measures that require a biometric capable device (such as your smart phone) and a login connected to it (Google, for instance, but passkey is becoming a more available option for logging into Facebook, Instagram and others).
Passkeys cut out the problem of phishing, which is the practice hackers and con artists use to discover or acquire your password through not-so-obvious methods, such as false URLS / links that appear to be legitimate, scam emails with links to login pages that appear to be legitimate but store your data for bad actors to access, phone calls asking employees for sensitive information while pretending to be a legitimate contractor or colleague with a reason to know.
Don't think that this just happens to the uneducated or simple. 1 in 2 organizations were exposed to this type of attack last year and, even if 1 in a 100 is averted without a problem, all it takes is one successful attempt to expose potentially billions of people to fraud and identity theft, blackmail, harassment, or worse.
Passkeys are easy to set up if you are given the option. You do need your smart phone or tablet handy if you choose this option, however, as your fingerprint will be used to login to desktop apps and PC software using the biometrics already on your phone. Quick, simple, and no one can (at least at the moment) get around pressing your finger to the fingerprint sensor remotely.
If you are given the option to set up a passkey, select this option and follow the instructions given by the platform for passkey login. Google Gmail login is one I personally use often. You can also setup pattern or pin login as a passkey rather than biometrics, but these methods are less secure.
The downside is that you will need to authorize each new device you get to share biometric data with whomever or whatever you choose to share a passkey with, backup of this information can be hard to acquire, and it is still worth it to allow some form of multi factor authentication, but the peace of mind and security is certainly worth the effort
We can expect to see this technology become more common place over the next 5 years and hopefully be more available on different platforms for security.
If you are looking to implement MFA or Passkey security measures for your business and employees, contact your agent to discuss options best suited for your needs or schedule your free consultation with us today.
Learn More About Passkeys and Current Security Options on the First Level:
- Duo - From MFA to Zero Trust - How to Gradually Implement New Security Measures
- Okta - How do Passkeys work and why do they matter? Passkey Primer
- Google - Passkeys and Passwordless Security
- FIDO Alliance - Passkeys
- Specorps - Passkeys: Benefits & Limitations
- Passkeys.com - Everything You Need To Know
All links open in new windows. Digital Saints Solutions is in no way affiliated with nor partnered with the entities above and provide this information purely to educate our clients and consumers.
3. Revoke Permissions For Unused Apps Asking For Sensitive Data
For the Consumer: Many of us use our phones to manage our lives, to stay in touch, to access social media, to shop, and perform mobile banking functions. If you are one of us, then you may have some apps currently dormant on your phone with permissions that are putting your data at risk.
This could be a simple transfer of your contacts to those who would use them for phishing leads or can be as nefarious as hacking your camera or web cam, smart home, and creating chaos on your network. We will talk more about the former later.
Let's talk about how you can pre-mitigate those potentially terrifying attacks and privacy exploits with simple vigilance.
- Revoke ALL old app permissions: This is something you can do on any device, including your PC or Mac. The process of revoking permissions or uninstalling apps depends on your operating system and device, but we provided some links here to walk you through it. For most iPhone and Android phone users, you can access individual permissions for each app by finding the app in the apps folder or tappiing and holding to view permissions.
- When selecting each permission, consider what the app does that you are granting each permission for. There may be a legitimate reason for a messaging app to access your storage to send media and receive it over data, it may also ask to access your microphone to record your voice for voice messages or AI assistant / talk to text. These all seem reasonable for a messaging app.
However, I would question why an app for photo editing would need access to my contacts or microphone unless the app has some kind of audio addition feature or share directly from app.
You will often be asked for more permissions than the app actually needs to function fully. To find out, use the app itself. If you select a function that you haven't granted permissions to the app to access the needed files or storage, you will be prompted to do so before you can continue. We recommend selecting the 'Only While Using The App' option, particularly in regards to your location data.
The app itself will typically provide an explanation as to why you should grant this permission. It is up to you if you choose to do so and if you don't feel comfortable, there are plenty of apps that could take its place.
- Regularly Patch & Update Your Devices- All operating systems are constantly updated with new patches that address security exploits or potential security risks before they can occur at a larger scale. As we have said before, never neglect to update your software when an update is available. Create backups if you are concerned about conflicts or problems caused by the new patch. Pay particular attention to optional patch updates with security reasons behind it. Having updated software closes a lot of past loopholes and back doors that have been used by hackers for years prior to success.
- Download Apps From Verified / Reputable Sources - The Google Play Store actually has quite robust security clearance and protocols for the apps and games it allows to be downloaded or purchased from the platform. While you may not be able to fully avoid downloading independent apks if you are more of an advanced user, if you are being prompted to download an app outside of the play store or Apple store, consider the possibility that that app may contain malware.
- Keep An Eye Out For Mismatched Extensions or File Type- For the longest time, Apple's iOS was untouchable and toured as the most secure option for consumers. Unfortunately, that is no longer the case. It was only a matter of time before someone discovered an exploit that was shared with several bad actors before being addressed by Apple, but harm had been done. This particular exploit was an executable (.exe) file that was disguised as an audio file that was uncommonly large. .exe files that have been acquired from an unknown source should be approached with caution if you cannot verify where they were obtained and this goes for all devices and operating systems.
When run through or launched by a media player, nothing would happen, but if a user were to open the file unknowingly, the malicious software would them be launched and installed, unbeknownst to you. Even uninstalling or deleting the file at that point would not remove the malware, as it would attach in the rootkit.
Newer versions of Android automatically archive and/or remove permissions from apps that have not been used for a long time. You can check this setting under the Apps banner in System settings.
Archived apps are no longer active on your device and will need to download patch files to run if you select them later. Archiving only stores core files to your device offline while removing permissions, data access, and functionality such as running in the background.
4. Protect Your Network With Practical Security Solutions
There is nothing more horrifying to us than the breaches of data privacy and virtual privacy that have occurred through the use of tools available for use by the public. No one is exempt from a potential home or business network attack and this type of data breach is a 'not even once', as the effects can be life changing, traumatizing, and catastrophic for the victims.
Picture this awful scenario: You are home with your family and the kids are off for Christmas break. Every one is settling in to watch a movie on your smart TV. You tell your Alexa to dim the lights to set the mood, turn the thermostat down, and lock the doors. Each of these items is located on your network.
Suddenly, your lights start to flicker. The room is becoming hotter. Alexa starts speaking in tongues. The children are upset, panicking. It's like your smart home has been possessed. Every attempt you make to regain control is thwarted until a filtered voice comes through your Alexa. They ask you if you were having fun.
Something similar to this situation happened to these victims - or even worse.
There have been more and more documented incidents of hacking personal webcams for nefarious reasons, creation of all revenge and blackmail websites against these victims, and the overall exploitation of our dependence on technology has become more frequent and more disturbing. (Read this terrifying article from CNET to reiterate our urgency)
If you would like more of an idea of how awful these attacks can be, we encourage you to check out these stories from the victims (at your own discretion)
•Hacked Home Cam Leads To Swatting / Livestream Police Raid - BBC
•Smartest Smart Home Hacks of All Time - And The Dumb Apps That Allowed Them To Happen -DLink
•10 Devices Used To Hack Your Home -CIAS.EDU
•Smart Home Tech Used Against Survivors of Rape, Stalking, Abuse- DomesticShelters
•Hackers Take Over Couple's Smart Home - CISOMAG
•How Likely Smart Home Attacks Are (Everything You Need To Know)- CNET
•IoT Hacking Victim 34 Yo Software Developer - LinkedIn* (Not verified)
When it comes to locking down your smart home if you choose to make your home Internet enabled and AI interactive, it can be as simple as setting up blackout times and as complex as setting up encrypted channels, but nothing will protect you as much as limiting access to your network, creating a secure network password, and practicing a few of these precautions so that your daily life can't be manipulated by someone with the means to do so - and it is shockingly easy to do.
Take this web search engine for instance. It is commonly used to search for items within images, such as identifying a painting you saw in the background of a friend's photo.
Unfortunately, it can also be used to gain access to your home security cameras, your smart devices on your network, and other online devices with simply the knowledge of the manufacturer that made it.
While you can't mitigate ALL attacks and potential threats, we can always do our best. In cyber and information security, authentic, honest, security software specialities, developers, and consultants will tell you there is always the threat and we won't ever be able to completely lockdown all the potential routes a bad actor may take - but we can certainly make it more difficult.
If you have a smart hub or a robust network of connected devices, consider the following for your safety and peace of mind:
•Create Hard To Guess Wifi Passwords & Use Guest Wifi Networks For Guest Access - Many ISPs offer the option to have a separate wifi gateway for your guests just like a restaurant or store may have that you can log into with or without an assigned password. These public networks are far less secure than a private network, but, when implemented in your home, they can prevent potential bad actors from gaining default access to your home network, thus allowing them the same access to your router or Wi-Fi settings that you would have as an administrator.
If you don't have the option of creating a Guest network gateway or your ISP doesn't allow this on your plan, you can always kick devices you don't recognize off of your network at a set time manually.
Most ISPs allow some kind of remote management over your network either through their specialized app or directly through the router or modem. You can find out if you can access your router directly by typing the IP address for your brand / model of modem or router - give this website a try if you can't find this information printed on the device itself.
Through the Wifi Networks direct address or ISP mobile app, you will often also see settings for booting users and devices you don't recognize, resetting your password, changing the security protocols, and more.
- You can also find this if you use a built in or desktop operated modem on Windows by using Command Prompt and typing /Ipconfig and enter. Your router's IP will be listed under Default Gateway. There may be other ways to do this depending on your machine and operating system.
That also brings us to another thing you should avoid doing.
2. NEVER Disclose the Brand or Manufacturer/ Model of Your Smart Home or Network Equipment. As we just mentioned, one can find your gateway IP address based on the make and model of your modem and router, and, as long as they're currently connected to your network, this allows them the ability to alter your router or modem setting from the default configuration page. They can bump you off your own network and potentially lock you out of your own home. This includes the make/ model of security cameras or software, your webcams, alarms, smart hub, etc.
Believe it or not, it's a super simple to do and requires very little technical know how to make your life a living hell as so many have witnessed first hand.
Many routers even tend use default IP addresses, such as 192.168.0.1 once you have the IP, simply copy paste into your web browser and use admin / admin to log in if the settings have not been adjusted.
3. Use A VPN or Proxy to Surf The Web and Stay Secure over Any network - VPN is a common go to that is an inexpensive, easy to manage and install security measure we recommend for any network, whether big, small, or personal. Using a VPN masks key metadata that is sent back and forth between providers when you access a website or join a new network, such as your personal device IP, IMAC address, and location. VPNs can't protect against human error, however, so we still encourage even VPN users to avoid accessing sensitive data, such as their mobile banking app, when connected to a public network.
VPNs are inexpensive, can be free in some cases and can be set up on any and all devices. Google supplies a VPN service through Google One that is default only for Pixel phone users. We recommend any of the following providers:
- NordVPN (All devices)
- SurfShark
- ProtonVPN (Also available for webmail encryption)
- TotalVPN (All devices)
- BitDefender VPN
4. Use Analog Fail-safes - This may seem like common sense, but attacks are exclusively via the world wide web. It is the risk we choose to take when installing smadt home management and compatible accessories. Web cam covers can be purchased or a simple piece of tape will usually suffice when you aren't using it. If you notice unusual activity on your device or network, boot everyone from the network, restart the modem or router, and change the wiFi password. If possible, choose a service provider with the most up to date security protocols in place for their networks.
Finally, some of these attacks are limited by the proximity of the attacker to the network and some may be acted on remotely by a complete stranger. For this reason, just be careful who you give access to your devices and your network to. Set up hard to guess passwords, two factor authentication, and multi factor authentication if possible. Use a SD card to store security camera footage rather than connecting any security camera to an app or cloud storage option. SD cards range in storage amount and can be written over, but prevent remote access through your network by allowing for an offline alternative.
One last thought - A lesser used alternative is the option of setting your smart home network up separate from the network you use regularly, which gives you the option of flipping the OFF switch when devices aren't being used or you see indications of a potential attack without cutting you and your family offline entirely. Talk to your Internet service provider about options for this.
Always ensure that you have backups of your most important assets and stay on top of which devices should be connected and what they are called / their IP or MAC addresses so that you can easily boot that which does not belong.
Spam Email Warning and Tips
Did you know that the average person's email inbox is about 45% spam?
In an independent study, groups reported up to 60% of email received in their inbox each as spam, with a 25% daily minimum on average.
We have all received unsolicited spam emails before. Since email became a standard for instant written communication and information sharing back in the early 1990s, the amount of spam circulating on the web has increased dramatically.
While we have come up with better protocols and algorithms to sort the junk mail from what people actually want to open in their email inbox, these efforts aren't perfect. In fact, you will still find a chunk of missed emails in your 'spam' or 'junk' folders that could be considered important or time sensitive.
It can be extremely difficult to differentiate, especially if you subscribe to email newsletters, use digital forms for data collection, or use one email address for the majority of your account registrations and activities online. So at what point does just annoying, inbox storage eating, relentlessly bumping spam email become a security threat to you or your business?
All spam can be considered a scam to some degree, but not every junk email is going to cause lasting issues. If you can identify threats, we can help with the next course of action to protect your digital assets.
1. Inspect the sender address for misspelling or misleading punctuation. Look for clues in the header subtext. These email domains will often include easily missed characters such as '.' in between letters of commonly used domains, like a.mazon.com. The domain may even be completely misspelled and if you should go as far as to open and 'reply' to these emails, you may notice a different reply to email address or BCC in the header. Sometimes an email may appear to be an official correspondence, but there will be a forwarding address that isn't immediately apparent. This can be indicative of a phishing attempt.
2. Ask yourself, 'Did I solicit this response or trigger an automailer in any way?' You most likely have. Many websites require an email address and the acceptance of terms that allow the organization to contact you by email, send you automatic newsletters, promotions, and other common communications. This may eat up your storage space, but they are typically harmless and if you're starting to get fed up, you can usually reply STOP or scroll down to the footer and find an 'Unsubscribe' option to opt out of any further email communications from that sender.
⚠️Most companies, including most utility companies and service providers will never initiate contact with you without you contacting first or performing some kind of confirmation - a purchase confirmation or an automatic payment receipt, an invoice for recent services - these things require your initiation. If you receive an email from a company or service provider you do business with regularly asking for payments, asking you to confirm your sensitive information - account information, address, social security number, etc- DO NOT REPY - mark the item as Spam and/ or report it to your data security team.
These emails are best ignored and left to rot in your spam folder until deleted, however, you can protect others and prevent possible security breaches before they happen by reporting the email to the official sender, that is, the real business the email allegedly came from so that they are aware and can take action. You can also report potential scam sites, malicious mailers, and phishing attempts to the FTC.
Finally, these emails require you to reply with the information requested, so as long as you keep that to yourself, they are safe to ignore.
3. Avoid opening attachments from unknown senders, following links from unknown sources, and disable HTML / scripts in your webmail or viewer settings. This is one that echoes true from back when email was associated with 'You've got mail.' Unfortunately, back then, most viewers did not have settings that prevented the display of HTML or the execution of scripts upon opening an email. Now, most webmail providers, Outlook and other POP3 services have settings that you can adjust based on the message or contact. Gmail has HTML blocked by default with the option to enable HTML given when you open the email.
4. Change your email account password often - AT LEAST once every 30 days and avoid reusing passwords or making your passwords too easy for bad actors to guess. We all have been there. We have thousands of accounts in our names these days how can anyone keep track of them all? With recent Google Chrome updates and the addition of Microsoft Hello on Windows 10+ operating systems, keeping your accounts secure AND easy to access without keeping a password journal is as easy as setting up a pin, facial unlock, fingerprint, or external security key.
Not only that, but many web browsers will auto generate secure and complex passwords for you, allowing you to save them in your account to access when you need them.
Passkeys allow for you to use the same login across accounts and devices with your facial recognition, pin, and/or fingerprint. This is potentially the most secure option for those who can opt in to it. If you can't utilize your passkey at work, your company may issue external security keys - flash drives that 'unlock' accounts inside the company network or within your clearance.
If you don't have the option to use either and wish to stick with the old fashioned way of creating and storing passwords, create a password (within the specifications) that contains a variety of punctuation, capitalization, and numbers, if possible. The more random the better. The best place to store them? I'm a physical notebook. I myself keep my password backups in a password journal like this one. You should keep this book in a safe place, such as a locked safe or somewhere that cannot easily be accessed. Update each account password as needed every time one is created or changed. Get in the habit of changing your passwords regularly.
If you're wondering what that has to do with the dangers of spam, it's quite simple. If you become the victim of a phishing scam, the bad actor now possesses a lot of your personal information. This often includes access to the email account itself. Setting up two factor authentication and alerts can help mitigate this risk.
If you see something, say something. If a phishing or scam email is circulating your business network, let your coworkers / employees know to flag and ignore it. Education and recognition are your first line of defense in the prevention of security breaches, fraud, data leaks, and malicious attacks on your databases.
5. Keep track of official communications when doing business over email. In this day in age, negotiations, contracts, and payments can all be done efficiently and remotely. This also leaves potential loopholes for bad actors to acquire your sensitive data with a bit of luck and social engineering.
The best practice is to keep these communications in a separate folder and approve mail from only known email addresses within the business. If anything seems suspicious or off, don't hesitate to give them a call and confirm.
That being said, even though it is ill advised, we often transfer sensitive information back and forth via email. There are ways to do this securely and safely and even free resources to do so for individuals and small businesses.
The following links provide apps and plugins tried and true by our agents that we recommend to lockdown your communications and data sharing. Digital Saints Solutions is in no way affiliated with nor do we receive compensation of any kind from any of the providers on this list. For more info on who we partner with, review our policies
🔗OneTimeSecret- FREE Encrypted, secure platform for sharing passwords, credentials, and other sensitive information with viewer control, automatic expiration, and encryption options upon sharing via email. Created by a third party, small business developer. Subscribers to the software may customize the domain from which the secret is shared and other enhanced security features.
🔗Proton Mail - Proton Mail offers a paid premium encrypted secure webmail platform and email server for enterprises and individuals. Enhanced security features are only accessible with paid accounts, but single email address without domain customization and limited storage may be created for free. PoP3/Outlook compatible. Cloud server and VPN service also available through this third party verified independent developer. Proton VPN is verified in the Google App store as being audited and deemed secure.
🔗DuckDuckGo & Aloha Private Browsers - Using a private browser prevents tracking cookies / spyware from attaching to your IP and bad actors from potentially gleaning information submitted through common web forms or checkout pages. Both developers are praised by others in the field for providing a neutral, private, and secure web browsing experience to individuals and companies with high security clearance. Aloha was recently audited and found secure by independent third parties to further back up the validity of the software. Both browsers are free to download and automatically send 'Do Not Track' notices to advertisers and bots.
🔗 Incogni - A relatively new company that has developed an algorithm that identifies data breaches and tags leaked, compromised, or old data for deletion, scouting the internet for unused, hacked, or compromised accounts on behalf of the user. This software isn't free, unfortunately. If you receive a lot of unwarranted, unidentifiable, and unwanted email coming from various sources or potentially bots, services like this can remove your data from offenders databases, including your contact information. There are many tools available such as this one on the web, we encourage users to compare benefits and costs.
🔗JotForm FREE Starter and Business Options - We hold a contract with JotForm for our clients as one of our many solutions used to protect and provide secure communications outlets, document sharing / file sharing, payment processing, and more. Using a contact form mitigates the ability of an algorithm or bad actor to grab your email address off of your websites which can be used as a gateway to your data. Jotform provides encrypted submissions, links to Google Sheets and database APIs, integration with apps like PayPal, Adobe, and MailChimp, allowing secure submissions, payment processing, database building, and more. We highly recommend this platform as a more affordable alternative to Typeform which offers similar tools with a more polished UI. Virtually any contact form API or setup - including Google Docs or Google Forms - can be used with unique ID, Captcha, email verification, encryption, etc. To create stronger security options for your business.
Every project, every individual, every product, every business, and every company is unique. Consult with a knowledgeable, experience agent FREE regarding your web security options, integration, and receive a tailored list of services and solutions matched to your needs at an affordable price. Contact Us now.
New Year, New You - Device Health & Storage Tips To Start 2025 Off Right
Make Your Devices Last Longer and Run Better - New Year's Tips To Keep Your Devices In Near Mint Condition
Do you have the same cellphone you had last year? What about two years ago? More? Most people upgrade or replace their current cellphone every 2.5 - 3 years, but we can look forward to this length of time increasing as the majority of technological advancement across the board is in cloud and AI development.
Your old laptop, cellphone, or tablet (so long as it's still supported by its operating system to receive updates / patches) may be hanging around for much longer, so long as the proper measures are in place to ensure it doesn't suffer any kind of motherboard, screen, or chip damage.
When mobile phones first made their way to the market, for the amount of money that it cost for both the service plan and the financing you would have thought you bought something that was akin to what we have now with all kinds of capabilities. It was, in fact, just a phone without a cord. That was it.
Now, our cellphones are more than just communication devices. For millennials, Gen Z, and the upcoming generations, these devices have become akin to a diary or journal, your wallet, your daily Newspaper, cable provider, community connection, and of course, your phone. Older generations have jumped on board, but have had less time for these devices to be integrated into their lives like they have with the former.
It goes without saying that your devices are important. Whether we're talking about your phone, tablet, desktop, or laptop, these core devices definitely hold more priority in your life than your Ring doorbell or smart fridge. They're your connection to all things that you care about. So it makes sense that you would want to devote some time into ensuring that they remain in the best condition possible.
There is nothing more frustrating than losing access to your apps, files, and communications. Not to mention, most of us are hard pressed to be able to remember anyone's phone number anymore. We rely on them, and this makes it even more devastating when something goes awry.
While we can't possibly address all the ways you can make your technology last longer and perform better, this list of tips include some that may seem like common sense and others that we promise you may not have thought of. Most of them can be applied to all your devices
With hardware taking the backseat to algorithm, cloud, AI, and other software developments, we can expect to see less innovation when it comes to changes or upgrades on new releases, meaning that you can essentially hold onto your devices longer than you could during the technology boom of the 2010s - with a bit of prep and caution.
- Restart your devices regularly. This is one of those 'common sense' tips that we know we should do but often don't or put off regularly. While your device will typically automatically restart after an update, it is good to restart your devices at least once a week. Even better, allow them a good 10-20 minute rest. The amount of heat from the battery, processing, and screen lighting will eventually destroy the chips and miniature parts within, taking years off the life of your device that can be mitigated with a short cool down period. The length of time matters. You don't want to shut down your device for a minute, thirty seconds, etc. As some devices have hard and soft reset thresholds built in based on the length of time they have been shut down before rebooting. So, yea, when tech support told you to unplug it, wait 15 seconds, and plug it back in, the 15 seconds was key.

Make these 5 habits a New Year ritual every year and enjoy more time with your devices and more storage space.
Stay Safe In Person and Online - Tips for A Secure Holiday Season
Scammers don't just exclusively use the Internet and there are many ways they can steal your identity, credit card number, or even your virtual account information while you're out and about. While we have made several advancements when it comes to card security and the level of encryption payment processors and financial institutions use, it isn't 100% hack proof and can never really be.
Security is a two way street, while one entity may put their best foot forward, the other may not always be on their A game. I have a few basic tips will help you keep your identity and finances safer as you go about your holiday shopping and travel this year that you don't even have to thank me for - but it's the best gift I can give you.
- 🎁Leave your cards at home. Almost every financial institution offers a virtual card or virtual wallet compatible card that you can add to your Apple Pay, Google Pay, Samsung Pay or any virtual wallet app on your smart phone. These virtual cards connect to your account, but do not reflect your actual card number and do not have any available account information in their data composition, thus making it much harder for a hacker or scammer to intercept or steal. Set up your virtual wallet of choice and use your phone to tap to pay at any retailer that accepts credit or debit cards.
- 🎁Use Credit instead of Debit and avoid entering your PIN. Credit card institutions provide more protection for fraud, reimburse victims, and will provide cars security services that a traditional bank or debit account cannot. Since credit isn't linked to your actual monetary wealth, a scammer or hacker stealing your credit card information can easily be rectified by cancelling the card, disputing or stopping the transaction, and contacting your credit card company. Not only this, but reimbursement is much easier to receive than if someone spends your entire bank account balance. If you don't have credit cards or don't have high credit limits, there are options for you as well.
- Avoid entering your PIN number into the terminal anywhere that isn't an authorized ATM attached to your financial institution, even if you are simply requesting cash back. Run your card as credit when asked to skip the pin entry or use your virtual wallet app. 🎁Only enter your card information for purchases through secured websites with encryption. You may notice a lock symbol in the upper left hand corner of a website running https protocols. You can click this icon and learn more about the way the website is encrypted and secured. Most banks use 256 bit level encryption, but this isn't entirely necessary for a merchant. Look for security details and verify the merchant before making your purchase. You can easily find business information online, including reviews and disputes made by customers.
- 🎁Use Screen Lock and 2 Factor Verification. Your phone is your life. If it's stolen or lost, there goes pretty much all of your sensitive information with it. For this reason, you should always use a screen lock. Biometrics work best as they are unique to you and allow you to create "passkeys' that can be used to unlock and access other accounts securely on other devices using your screen unlock method on your phone. Enable 2 Factor Verification for your accounts in the event that your device is compromised or even just for data. This can be done using a phone number or third party authenticator app. Some platforms also use methods like back up codes. Keep any and all of this information safe by printing it out, storing it in a physical file folder, and removing digital copies.
- 🎁Don't post your vacation plans or location on social media. Avoid responding to posts that ask questions about your birthday, full name, etc. Social Media platforms like Facebook and Instagram are set up to attach your location to your posts unless you disable this feature. If you plan on going away for the holidays, don't let would be burglars get a heads up by letting them know exactly how long you plan to be away lest you awaken Christmas morning to the tree and the presents missing. This may seem like common sense, but it's amazing how many people still post their whereabouts in ways that could result in break ins or even potential aggressive robberies.
- Make sure these settings are disabled on your children's profiles as well as your own or limit exposure to people that you know well using privacy and blocking settings. The second thing refers to popular 'games' on social media that will ask for these items to discover your 'spirit animal' or something of the sort. Many times, the responses to these questions are easily the answers to security questions that platforms use for account recovery. While it may seem innocent, consider who can access this information before you post it and how it may be used.
-
🎁Take advantage of Informed Delivery, tracking, and in person package pickup services. If you suspect you have porch pirates or want to preemptively keep your packages safe for yourself or the person you have sent to, there are several free ways to help avoid the situation entirely. Most couriers will allow a ship to store option for consumers, often for no additional cost. You may select this option when purchasing a shipping label online or request it in person. This way, they will hold the package when it arrives until you can physically pick it up in person, completely avoiding the situation where your package is left out as porch pirate bait. If you don't like this option or can't easily access your local post office, UPS store or FedEx location, another option offered by USPS and (in some form) by other couriers is informed delivery. Informed delivery will notify you when a package is ready to be delivered and in the possession of your mail delivery person. From the link in a text or via email, you may arrange for them to hold the package or reschedule the delivery when you will be home to snatch it up before anyone else does. If you don't sign up for this, you can still sign up for free text alerts from all of these services on their website to receive updated shipping and delivery info for yourself and those you may ship to.
Before we conclude, I wanted to address those who may be thinking cash is still king when it comes to avoiding some of these things. While cash is indeed a secure option from the data side of things, unfortunately many stores and companies will not always accept cash payments, particularly if change is needed or if using a self checkout. Many organizations have also stopped accepting bills larger than $20 denominations due to the high level of counterfeit fraud, particularly during the holidays.
If you don't use a bank or credit card, you still have the option of using a prepaid debit card, many of which are sold in popular grocery stores and are provided by well kowm companies like PayPal or NetSpend. Prepaid cards allow you to use digital payment options and make purchases online with a preset amount you can either "load" onto the card in-store using cash or transfer onto the card from your bank account. These cards can still be skimmed or hacked and aren't 100% secure in that regard, however, if you want to make secure purchases using a card or set a budget for your holiday spending, purchasing a prepaid Visa or MasterCard could be the best option for you.
🎄And with that, we wish you a safe and secure holiday season. May you have a wonderful Christmas and happy New Year!
Beware of Scams & Fraud This Holiday Season
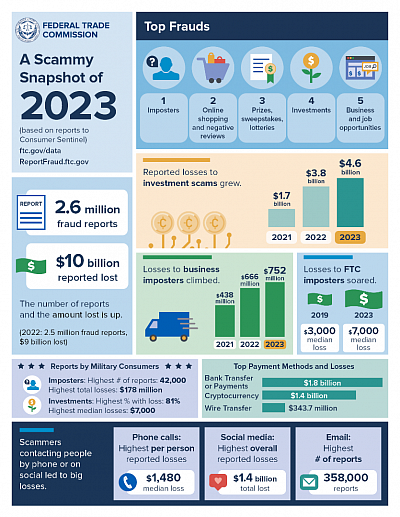
In 2023, victims reported losses up to $10 billion dollars to scams, the highest amount ever reported to the FTC. A 14% increase from 2022.
(Image source and data from ftc.gov)
When we think of hackers and con artists, we usually don't picture the kid next door that goes our lawn or the mailman that has been delivering our mail since we moved in to the neighborhood.
The reality is that ANYONE could potentially be a scammer, con artists, fraudster, or even a malicious hacker just like anyone can become a victim of their craft.
People also tend to think that only 'stupid' people fall victim to these crimes, and, while scammers overseas will often brag about how 'stupid Americans are' indeed, truthfully it has nothing to do with intelligence, race, gender, or nationality.
Businesses and individuals must be vigilant when it comes to education and protecting themselves from these "attacks". In many cases, even intelligent individuals find themselves dealing with the fallout from a scam or loss of account control, stolen identity, and other fraud.
The persons enacting these crimes are constantly updating their software and their methods, educating eachother and sharing information. One of the most common mistakes is that you have to 'initiate' the scam or performed some kind of action that resulted in the wrong people getting your sensitive information. Unfortunately, it's not as easy as avoiding specific websites or watching for signs that a form is legitimate or not. While being savvy as to some of the tactics these individuals use is definitely helpful, it won't prevent all potential avenues that can be used to lure victims into participating in their master plan.
From legitimate data centers or call centers, your first name, last name, and phone number is easily bought and sold by criminals from legitimate businesses with bad actors within them. Information and data sent between verifiable institutions such as banks can be intercepted and used to make victims think that they are dealing with a legitimate business or customer service agent.
The holidays is always a crucial time to be on alert and to proceed with caution when it comes to safe guarding your data and using precautions to protect yourself from these bad actors. With several thousand transactions taking place each day leading up to Christmas in brick and mortar stores and online, it isn't surprising that scammers and hackers take advantage of all the holiday chaos.
As a public service and to safeguard our clients, your clients, and employees, we want to share some resources and information that could save you the headache and financial turmoil of becoming a victim.
While we cannot possibly present every scenario or advise you on how to proceed in every situation that a scammer could come up with, we are well aware of several strategies and methods used by these bad actors and there are ways to throw them off or avoid the potential data loss all together.
As a side note, the best weapon we have against these individuals is education. The elderly are often targets because they typically aren't tech savvy and have a completely different worldview from growing up in a different era that makes them vulnerable. Education is the best tool we have to fight these individuals looking to take advantage of others and we encourage anyone reading this to pass on this information to friends, family, coworkers, bosses, and so on.
You really just never know who could be next and a lot of these crimes go unreported as the victims feel embarrassed or stupid for falling for it. There is no shame. If you are intelligent, they have to be just as intelligent to get to you if not more so.
These players have been playing the game much longer than you have and it's definitely rigged in their favor.
- 🔐Write your passwords down in a ledger with your other credentials. Keep the ledger updated. It's easy to store passwords in your Google account or on your devices, but unfortunately this allows a backdoor for someone that has access to your email or your device to now access the account information you have stored on it. No database is 100% safe and hack proof these days, but pen and paper stored in a safe place (not under the keyboard or somewhere people often hide passwords!) cannot be accessed online or through a network account.
- 🔐Update / change passwords often. This also seems like an annoyance and a pain in the butt that many of us circumvent when password expiration is enforced by our workplace or a specific website. However, changing your password often (and using this opportunity to log out from all devices signed in to that website) can save the headache in the future if someone has unauthorized control / usage of your account. It is important to make each password unique and not a reiteration of the last five passwords, as well. This makes your passwords harder to guess and will kick anyone that you don't want logged into your accounts off of them. Try and change your passwords every 30 days as a general rule of thumb. Avoid common terms and passwords that can easily be guessed. Use combinations of letters, numbers, and symbols (when allowed) to create a difficult to guess password that is also hard to crack, but not impossible. This can significantly reduce the damage of hacked accounts and prevent them, but a determined hacker can always discover the new password. You can never create a hack proof password, but you can make it very hard to do so.
- 🔐Be suspicious of random calls from banks or seemingly legitimate companies discussing your accounts(s) or requesting sensitive or personal information. The most recent scams have come from seemingly legitimate sources, but they always will either originate from a call or end in one. Scammers know that once they get the victim on the phone they can use charm and intimidation to get the victim to perform the tasks they require from them or share key information they can use against them. Remember, no business, bank, government institution, or legitimate business organization will call you 'out of the blew' without your initiation.
For example, if you request a call back from your financial institution for support and they return your call, that is more likely to be a legitimate call than one made without your knowledge or initiation. Always check the company policies as many will state they will never call you and ask for personal or account information over the phone.
In fact, if you are to receive communications by phone, text, or email from nearly any company in the USA you will have to physically 'opt in' to receive them and those settings can also be verified.
🔐See this list of the 9 Most Common Call Scams from Synchrony Bank
- 🔐Beware the Long Cons. Relationship / Romance Scams fit this bill. These scammers are patient, cunning, and will put victims in situations where they may be perceived as an accomplice or they may unknowingly implicate themselves in the crime by laundering money for the scammer or performing other activities to facilitate the scam.
These people often troll dating websites and apps looking for lonely, often elderly singles (but not always - check out this article) that they believe may have a bit of wealth or even younger, accomplished singles - men and women alike. They will create a fake profile that seems appealing to their targets, sometimes even pretending to be celebrities or well known persons, using photos they have stolen from legitimate accounts or tabloids. They will lead the victim to believe that they care about them, develop an ongoing relationship with them, and when they feel the victim is comfortable with them, they will start requesting sums of money for 'travel expenses' or make claims that they need to pay medical bills, can't pay their mortgage, etc.
These scams can lead not only to financial loss and emotional damages, they have even lead to criminal charges and even death for those unfortunate enough to be caught in them.
Just like a bad relationship, it can be very hard to cut ties with the scammer as they will often retaliate in a nasty way.
If you or someone you know (or you suspect may be) a victim of a scam like this, click here. If you are a dating site / app user and want to know how you can protect yourself, click here.
- 🔐Verify URLs, do not click / tap URLs in texts from anyone you don't know and double check email addresses before following links or downloading attachments. This is easier said than done and because of the prevalence of these 'phishing' and ransomware scams, scammers have found new ways to get around even the most savvy and vigilant consumers. If you received an unwarranted email or text from what seems to be a legitimate company regarding anything from a missed package 📦 text from USPS or a refund response from Amazon, check the sender - either the email address or phone number. Many times you will notice that the address has some kind of alteration, a misspelling, a dot where their normally wouldn't be, or the attachment/ URL doesn't appear to have anything to do with the alleged purpose of the text or email. If you suspect that you received something strange, always contact the company directly using the contact information on their official website. They will be able to verify the information in their systems (or not).
- 🔐But, do really double check that email address or phone number. Recently, my hometown experienced a scam at a local public highschool that had contracted a construction company to do something for the school. The accountant in charge of paying the invoices received an email from what appeared to be the person they had contracted regarding payment methods for the invoice that they had received. This seemed to be legitimate because the individual had been emailing the contractor back and forth about this the previous day and thought nothing was out of the ordinary when she submitted the cheque using the method the alleged contractor supplied here. The actual contractor eventually followed up and that was when the school realized they had just hired thousands to some account in Africa. This is called interception and it has become more and more prevalent recently. All a scammer needs to do is have access to your inbox or some knowledge of your current communications and affairs to interject their fake email in a way that appears consistent with your conversation. This further reiterates the need to change your password to something hard to guess often and log out of your accounts often along with verification and vigilance.
- 🔐Update Your Operating System, Apps, and Software. Not everyone needs a complex antivirus license unless you use your home network for work or perform work that includes the usage, viewing, and transfer of sensitive information. Everyone has heard of ransomware attacks against companies and organizations, but the key to preventing these attacks is often very simple. Hospitals, municipalities, and public schools are often prime targets for these attacks as hackers take advantage of the backdoors and exploits within older software and operating systems that have been fixed or addressed in newer updates / versions. Keeping your software up to date on all of your devices can help keep you secure at home and at work. Seems simple enough, yet many big corporations (even our government at times) neglect this simple yet crucial part of device maintenance and security.
The fear that the update may cause data loss or incompatibility issues is largely unfounded when compared to potential ransomware attacks, where, in several cases, victims aren't able to recover their systems even after the ransom has been paid.
For the record, I am referring to critical updates. Many developers will release optional updates or patches for operating systems and software that you may defer or postpone for a bit (or indefinitely). As Apple has admitted to creating their own system lag and eating memory when it comes to updates for their older devices, it isn't a surprise that Apple users are the most apprehensive to do so. While Apple devices are considered secure due to the nature of the operating system and encryption, these devices can still be hacked and more and more exploits are becoming available for Apple software. So don't wait, do the update.
- 🔐If they want a wire transfer or gift card payment, It's not legitimate. Back in 2015, I worked as a customer service manager at a local grocery store where my duties included lottery printing and redemption, scratch off sales and redemption, tobacco sales, Western Union transfers, payouts, and money orders, as well as being the person that you went to if you needed assistance or had something to return. I typically ran the counter by myself and multitasked, taking several people at once. I remember it was close to Christmas just like it is now and this older gentleman came in the front doors which had him pass by where I was working the front desk.
He was on the phone with someone and I could tell he was confused and hesitant. He kept asking whoever was on the other end to repeat what they were saying, but I caught the beginning of the call when he came through the doors. This man had received what he thought to be a legitimate email from Amazon claiming that his 'HD Television purchase has been completed'.
If you guessed it, he didn't buy a TV from Amazon. So this gentleman was thinking someone has purchased this television on his dime somehow and he needs to contact Amazon to cancel the order and get his refund. This is exactly what the scammer wanted him to do. They knew that he would see the email and immediately take action to 'get his money back.' They provided him with a fake number that directed to them where they pretended to be Amazon customer service reps.
At some point, the scammer had instructed this man he needed to pay a fine to receive his refund.
The scammer told the man he would accept specific types of gift cards, such as Google Play or Best Buy gift cards.
When the man got confused and started asking questions, the scammer switched off his nice customer service character and began to lean into this man in an attempt to pressure him to make the purchase.
The scammer wanted to keep him on the phone throughout the process to ensure that he was doing what the scammer instructed. The scammer knows that if they can keep the person on the phone, they are more likely to do what they want.
I got the older man's attention and waved at him, all but screaming at him over my customers in line to hang up and that it was a scam. Finally, he turned from the gift card rack and saw me. I could see the look of understanding on his face and he shifted gears, "I do not think that we need to be discussing this any further, goodbye," and he hangs up.
He was shaken, obviously. He barely muttered a thanks to me before he walked back out the doors. It was understandable. He came really close to making the first move that could have lead to a domino effect. Scammers will always try and get you for more if they have had success.
They will threaten you and make comments that can lead you to believe you and your family are being surveilled even if they gleaned this information from something you posted on Facebook and forgot about. He did come back and thank me in person, face to face thereafter. I was just happy that I could prevent it from happening.
Unfortunately, I have had more instances where the person making the purchase is so intimidated or convinced that they have to do this that they will lie and argue with those trying to prevent them from being taken advantage of, defending the purchase of 5 $500 Best Buy gift cards to even their financial institution, which will often decline this type of transaction initially.
No legitimate business or company, organization, or independent contractor will request that you pay them in gift cards of any kind. Scammers ask for this form of payment because once it's purchased, it is virtually untraceable. If it doesn't sound right, it probably isn't.
🔐Another common relevant scam will involve Western Union Wire Transfers. Scammers will request that the victim pays them in a wire for whatever reason. They will usually provide a fake name and dummy address or use another victim's information and have them pick up the funds to provide the scammer another layer of security. These scammers will call pretending to be your utility company or even a government agency, demanding payment for accounts unpaid. As mentioned before, these entities will never randomly call you - even to demand payment. If you are unsure, look up the company or agency in question and verify the information with them. In many cases, you will find that they don't even accept Western Union payments